AWS Security Token Service (STS)
AWS Security Token Service (STS) is a web service that enables you to request temporary, limited-privilege credentials for AWS IAM users or federated users. It is used to grant access to AWS resources based on temporary credentials, which is ideal for scenarios where users or applications need temporary access to AWS resources or services.
Key Features
- Temporary Security Credentials: Issue temporary credentials with defined permissions, expiration time, and scope for secure access to AWS resources.
- Federated Access: Allow users from external identity providers (e.g., Google, Facebook, or corporate directories) to access AWS resources using federated identities.
- Role Assumption: Enable users or services to assume roles with specific permissions, making it easier to delegate access within AWS accounts or across accounts.
- Session Duration: Control the duration of the temporary security credentials, with a maximum validity of 12 hours for most operations.
- API Operations: Access key STS API operations including `AssumeRole`, `GetSessionToken`, and `AssumeRoleWithWebIdentity` for obtaining temporary credentials.
Common Use Cases
- Temporary Access: Provide temporary access to AWS resources for applications, users, or third-party services, reducing the risk associated with long-term credentials.
- Cross-Account Access: Enable users or services in one AWS account to access resources in another account by assuming roles.
- Federated User Access: Allow users from external identity providers to access AWS resources without needing an IAM user account in AWS.
- Secure API Access: Use temporary credentials to secure API calls and operations, enhancing the security posture of your applications.
- Role Delegation: Delegate specific permissions to other AWS accounts or services, allowing controlled access to resources and actions.
Architecture Overview
The following diagram illustrates the architecture of AWS Security Token Service (STS):
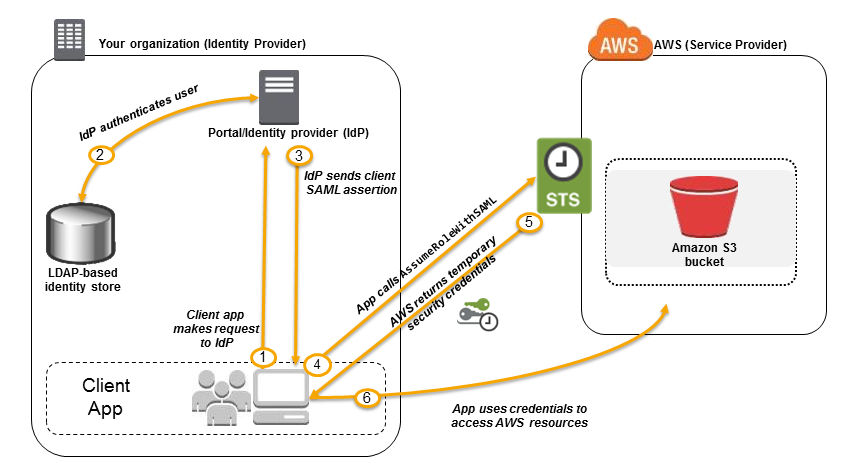
- STS Request: Clients make API requests to STS to obtain temporary security credentials.
- Temporary Credentials: STS issues temporary credentials with a defined expiration time and limited permissions.
- Role Assumption: Users or services assume roles and receive temporary credentials for accessing AWS resources.
- Federated Access: Users from external identity providers are authenticated and granted temporary credentials for accessing AWS services.
- Session Management: Credentials are managed and validated by AWS STS during their validity period.
Integration with Other AWS Services
AWS Security Token Service integrates with several AWS services to provide secure, temporary access:
- AWS IAM: Use STS with IAM roles to delegate access and manage permissions for AWS resources.
- AWS Lambda: Use temporary credentials to access other AWS services or resources within Lambda functions.
- AWS CloudFormation: Enable cross-account access and resource management by assuming roles in CloudFormation stacks.
- AWS CodePipeline: Manage access to deployment resources and other services using temporary credentials in CI/CD pipelines.
- AWS S3: Use temporary credentials to securely access S3 objects and perform operations without long-term credentials.
Things to Remember for the Exam
- Temporary Credentials: Understand how STS issues temporary credentials and the benefits of using them for secure, short-term access.
- Role Assumption: Be familiar with how to use `AssumeRole` to grant temporary access to AWS resources across different accounts or within the same account.
- Federated Access: Know how STS integrates with external identity providers to enable federated user access to AWS services.
- Session Duration: Remember the maximum duration for temporary credentials and how it affects access control and session management.
- API Operations: Review the key STS API operations such as `AssumeRole`, `GetSessionToken`, and `AssumeRoleWithWebIdentity` for obtaining and managing temporary credentials.
- Security Best Practices: Understand security best practices for using temporary credentials and managing roles and permissions effectively.